使用 vlx-vmengine 进行反混淆。
vlx-vmengine-jvm 是一个用 Java 实现的 Java 字节码执行引擎。请参阅 https://github.com/vlinx-io/vlx-vmengine-jvm 因为它的用途。
有一段简单的 Java 代码如下:
class HelloWorld {
private String name = "";
public HelloWorld(String name){
this.name = name;
}
public void sayHi(){
System.out.println("Hi, " + name);
}
public static void main(String[] args){
String name = "George";
HelloWorld hello = new HelloWorld(name);
hello.sayHi();
}
}
经过编译成类文件并使用某种混淆引擎进行混淆后,得到以下文件:
使用 jadx 打开后发现,除了 main 函数,所有其他信息都无法识别,字符串已被加密。
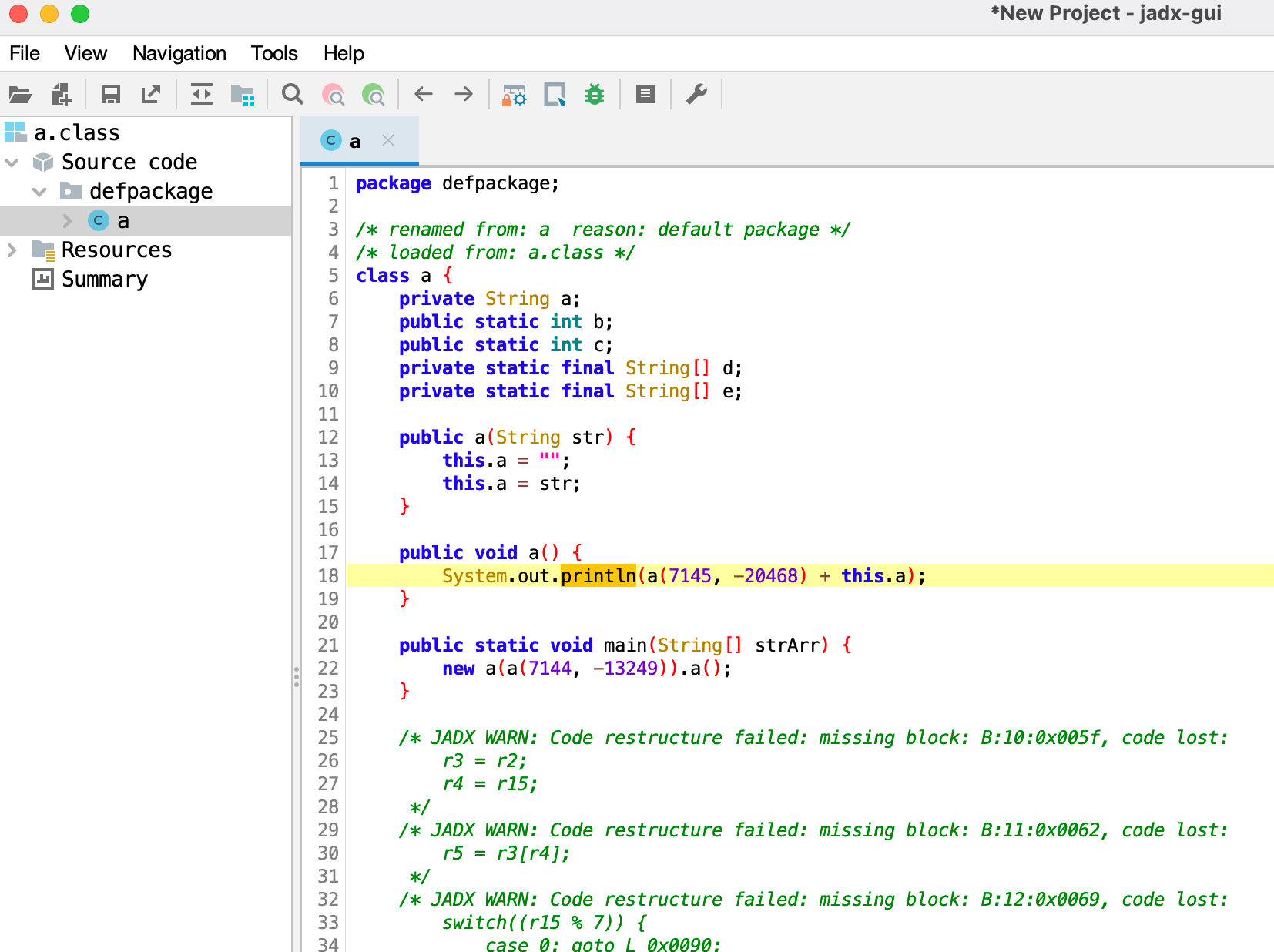
然而,即使感到困惑,类和字节码信息的基本结构仍然存在。使用 类查看器 打开 a.class您可以查看该类的方法和字节码信息。
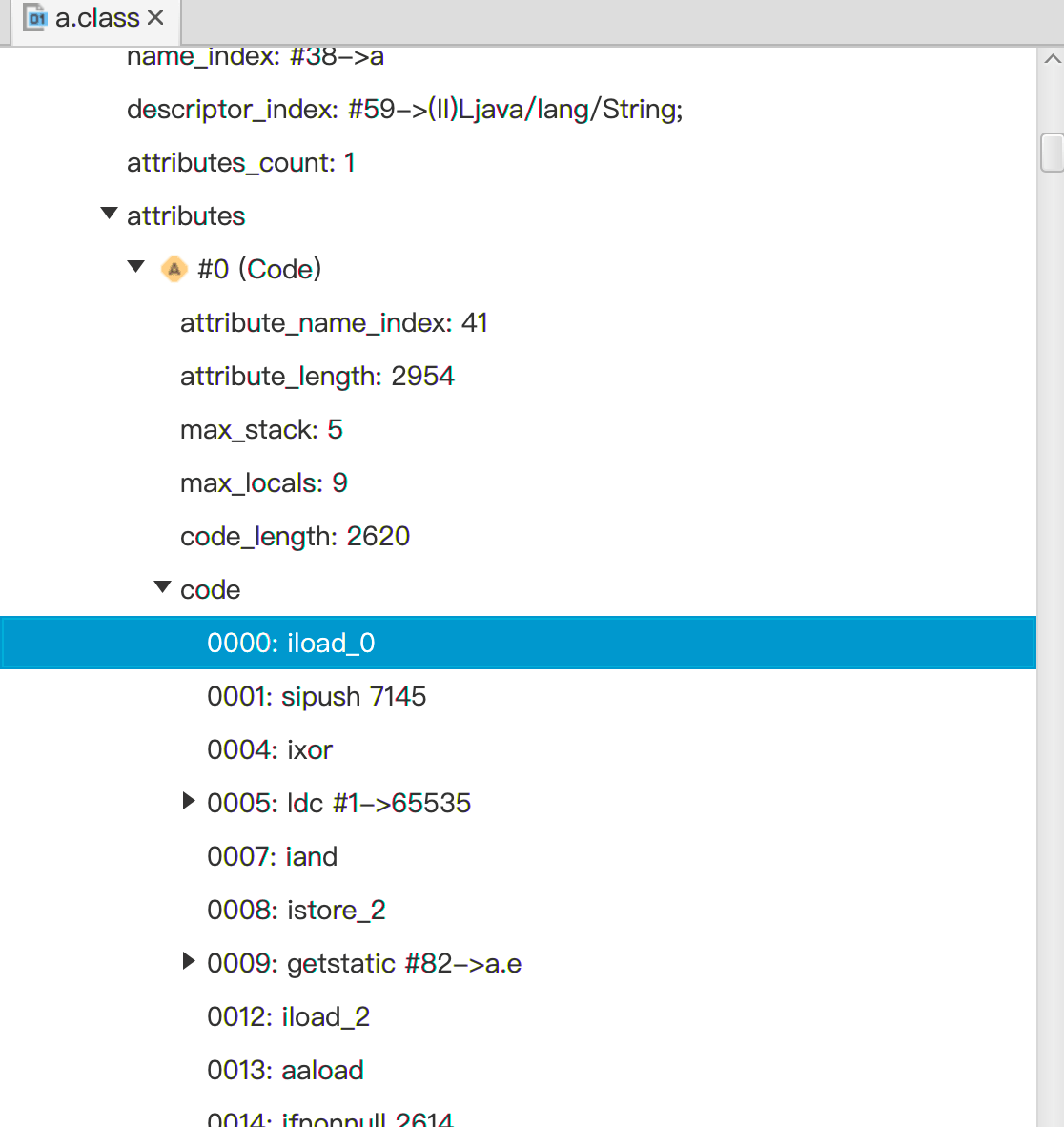
无论如何混淆,都只能在静态层面上混淆代码,增加分析的复杂性。在动态执行过程中,仍然需要恢复程序的原始运行逻辑。使用 vlx-vmengine-jvm 运行混淆后的代码…… main 采用这种方法,我们得到以下输出
2023-05-21 18:19:05 [DEBUG] LocalVars: [kotlin.Unit, kotlin.Unit, kotlin.Unit]
2023-05-21 18:19:05 [DEBUG] "L0: SIPUSH"
2023-05-21 18:19:05 [DEBUG] "push" 7144
2023-05-21 18:19:05 [DEBUG] "L3: SIPUSH"
2023-05-21 18:19:05 [DEBUG] "push" -13249
2023-05-21 18:19:05 [DEBUG] "L6: INVOKESTATIC"
2023-05-21 18:19:05 [DEBUG] "#20"
2023-05-21 18:19:05 [DEBUG] "class a, NameAndType(name='a', type='(II)Ljava/lang/String;')"
2023-05-21 18:19:05 [DEBUG] private static java.lang.String a.a(int,int)
2023-05-21 18:19:05 [DEBUG] "pop" -13249
2023-05-21 18:19:05 [DEBUG] "pop" 7144
2023-05-21 18:19:05 [DEBUG] Execute method: private static java.lang.String a.a(int,int)
2023-05-21 18:19:05 [DEBUG] Args: [7144, -13249]
2023-05-21 18:19:05 [DEBUG] "push" "George"
2023-05-21 18:19:05 [DEBUG] "L9: ASTORE_1"
2023-05-21 18:19:05 [DEBUG] "pop" "George"
2023-05-21 18:19:05 [DEBUG] "localVars[1] = George"
2023-05-21 18:19:05 [DEBUG] "L10: NEW"
2023-05-21 18:19:05 [DEBUG] class a
2023-05-21 18:19:05 [DEBUG] "push" InstanceToCreate(clazz=class a)
2023-05-21 18:19:05 [DEBUG] "L13: DUP"
2023-05-21 18:19:05 [DEBUG] "pop" InstanceToCreate(clazz=class a)
2023-05-21 18:19:05 [DEBUG] "push" InstanceToCreate(clazz=class a)
2023-05-21 18:19:05 [DEBUG] "push" InstanceToCreate(clazz=class a)
2023-05-21 18:19:05 [DEBUG] "L14: ALOAD_1"
2023-05-21 18:19:05 [DEBUG] "#1"
2023-05-21 18:19:05 [DEBUG] "push" "George"
2023-05-21 18:19:05 [DEBUG] "L15: INVOKESPECIAL"
2023-05-21 18:19:05 [DEBUG] "#47"
2023-05-21 18:19:05 [DEBUG] "class a, NameAndType(name='<init>', type='(Ljava/lang/String;)V')"
2023-05-21 18:19:05 [DEBUG] public a(java.lang.String)
2023-05-21 18:19:05 [DEBUG] "pop" "George"
2023-05-21 18:19:05 [DEBUG] "Execute new instance: public a(java.lang.String)"
2023-05-21 18:19:05 [DEBUG] "Args: [George]"
2023-05-21 18:19:05 [DEBUG] "pop" InstanceToCreate(clazz=class a)
2023-05-21 18:19:05 [DEBUG] "L18: ASTORE_2"
2023-05-21 18:19:05 [DEBUG] "pop" a@4612b856
2023-05-21 18:19:05 [DEBUG] "localVars[2] = a@4612b856"
2023-05-21 18:19:05 [DEBUG] "L19: ALOAD_2"
2023-05-21 18:19:05 [DEBUG] "#2"
2023-05-21 18:19:05 [DEBUG] "push" a@4612b856
2023-05-21 18:19:05 [DEBUG] "L20: INVOKEVIRTUAL"
2023-05-21 18:19:05 [DEBUG] "#54"
2023-05-21 18:19:05 [DEBUG] "class a, NameAndType(name='a', type='()V')"
2023-05-21 18:19:05 [DEBUG] public void a.a()
2023-05-21 18:19:05 [DEBUG] "pop" a@4612b856
2023-05-21 18:19:05 [DEBUG] Execute method: public void a.a()
2023-05-21 18:19:05 [DEBUG] Receiver: a@4612b856
2023-05-21 18:19:05 [DEBUG] Args: [a@4612b856]
Hi, George
2023-05-21 18:19:05 [DEBUG] "L23: RETURN"
从控制台输出可以看出,程序已恢复其原有行为,即打印内容。 Hi, George同时,从输出结果中我们还可以看出,字符串解密函数位于 private static java.lang.String a.a(int,int),带有参数 7144 和 -13249如果我们继续使用 vmengine 进行调试 a.a(int,int) 通过这种方法,我们可以发现该混淆引擎使用的字符串加密方法。