Cracking encrypted Java applications using jhsdb (hotspot debugger)
One solution for Java code protection is class file encryption or jar file encryption. This type of solution loads the encrypted class file or jar file through a self-defined loader, which is useless due to the existence of the JVM’s Attach mechanism and can be easily cracked with the tools that come with the JDK.
Sample Application
Below is a sample application with a simple swing window and a button. https://github.com/3-keys/test-swing-app
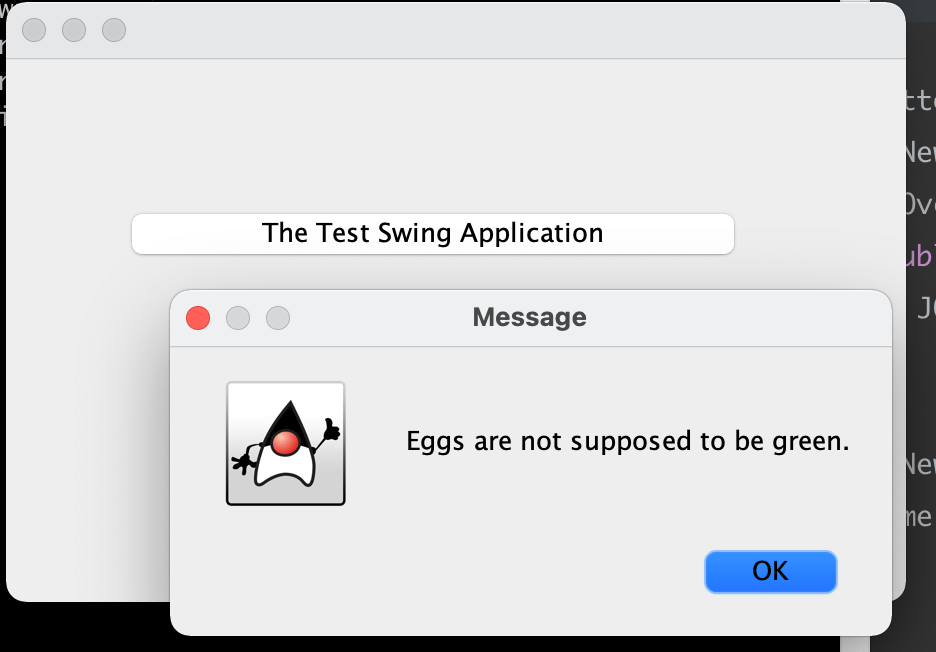
Encrypt Application
Export a runnable jar file with Eclipse and use an encryption tool to encrypt the jar file. After encryption, the structure of the jar file is as follows:
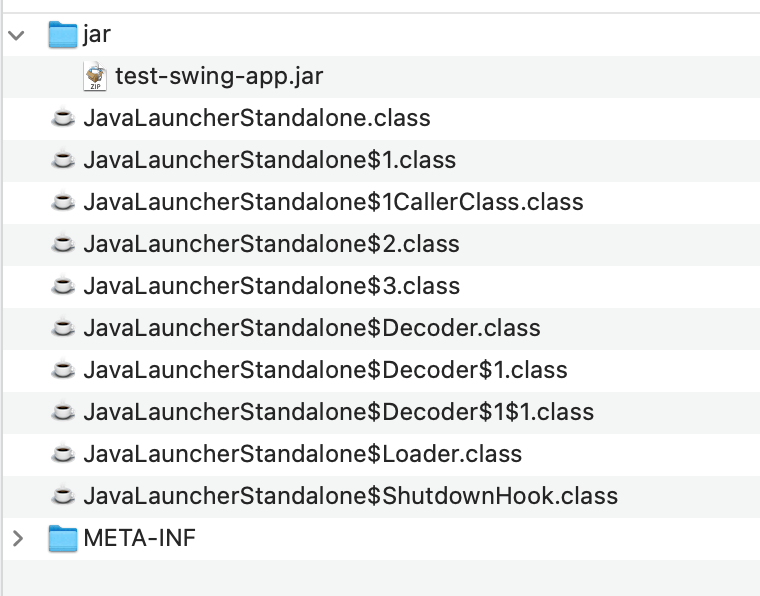
test-swing-app.jar is the encrypted jar file data, the Launcher classes are the custom loading classes of this tool, and the encrypted jar package is still run through the standard java -jar command
Crack the encrypted application
First, run the encrypted jar file, then find the bin directory of JDK and you should be able to find a jshdb file.
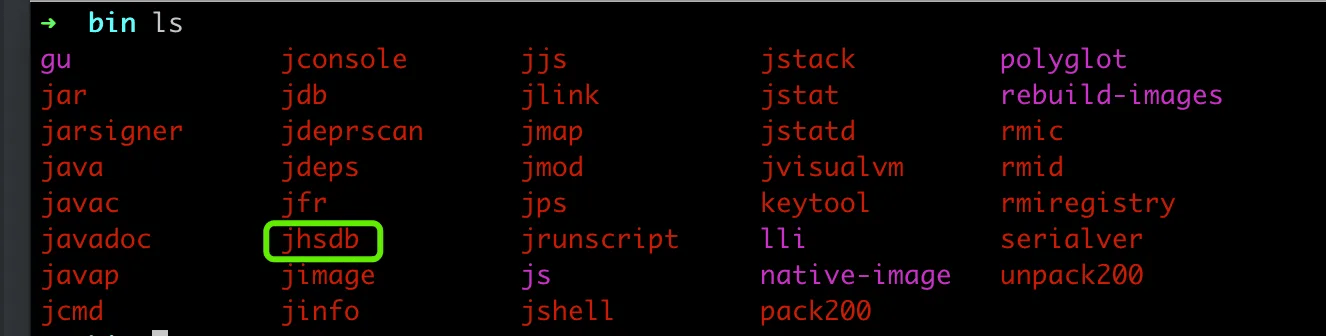
Execute jhsdb hsdb, open HotSpot Debugger, if it is under Windows, you may need to run as administrator, click File to select Attach to HotSpot process…,
Use the ps aux | grep java command in Linux system, and find the process pid through Task Manager in Windows system. Enter the process pid in the dialog box below.
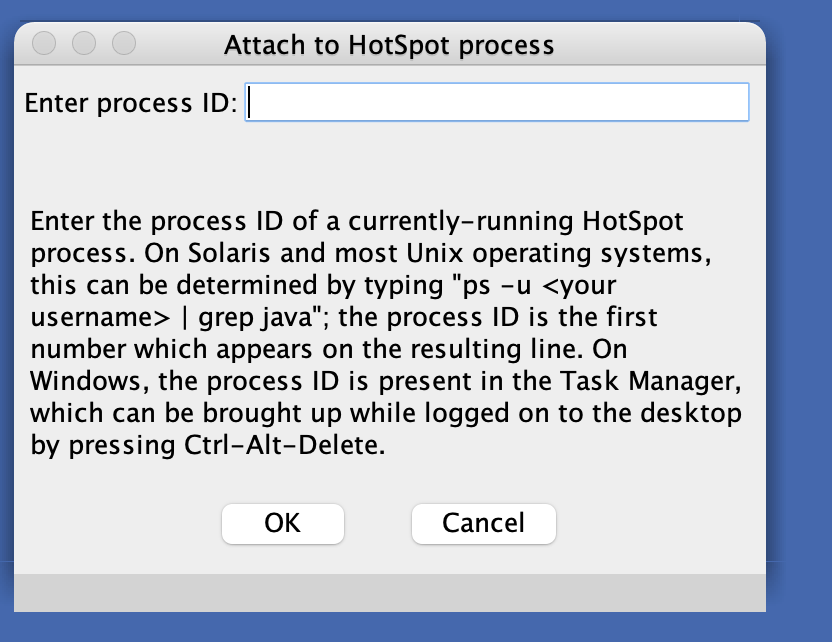
After successfully attaching it, click Tools->Class Browser
The class Browser contains information about all loaded classes, search for com.example and you may see all the classes under com.example
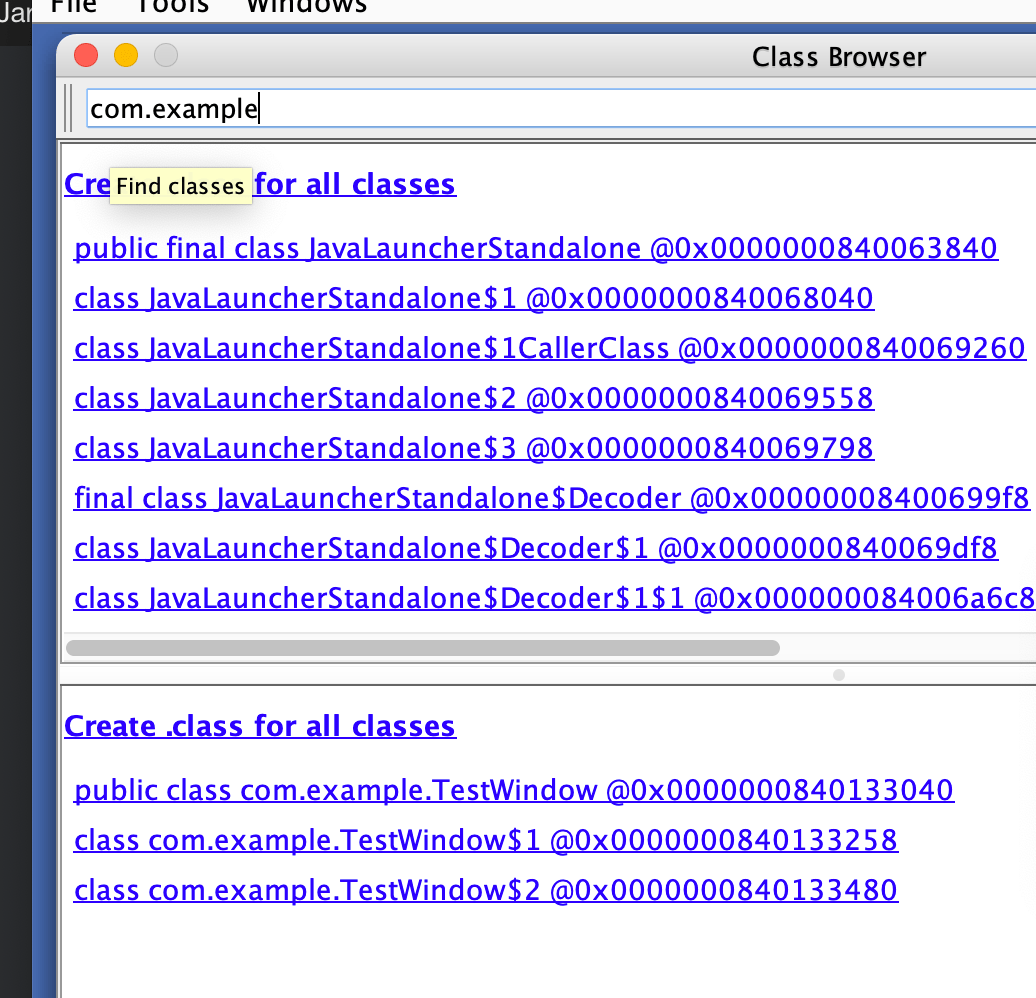
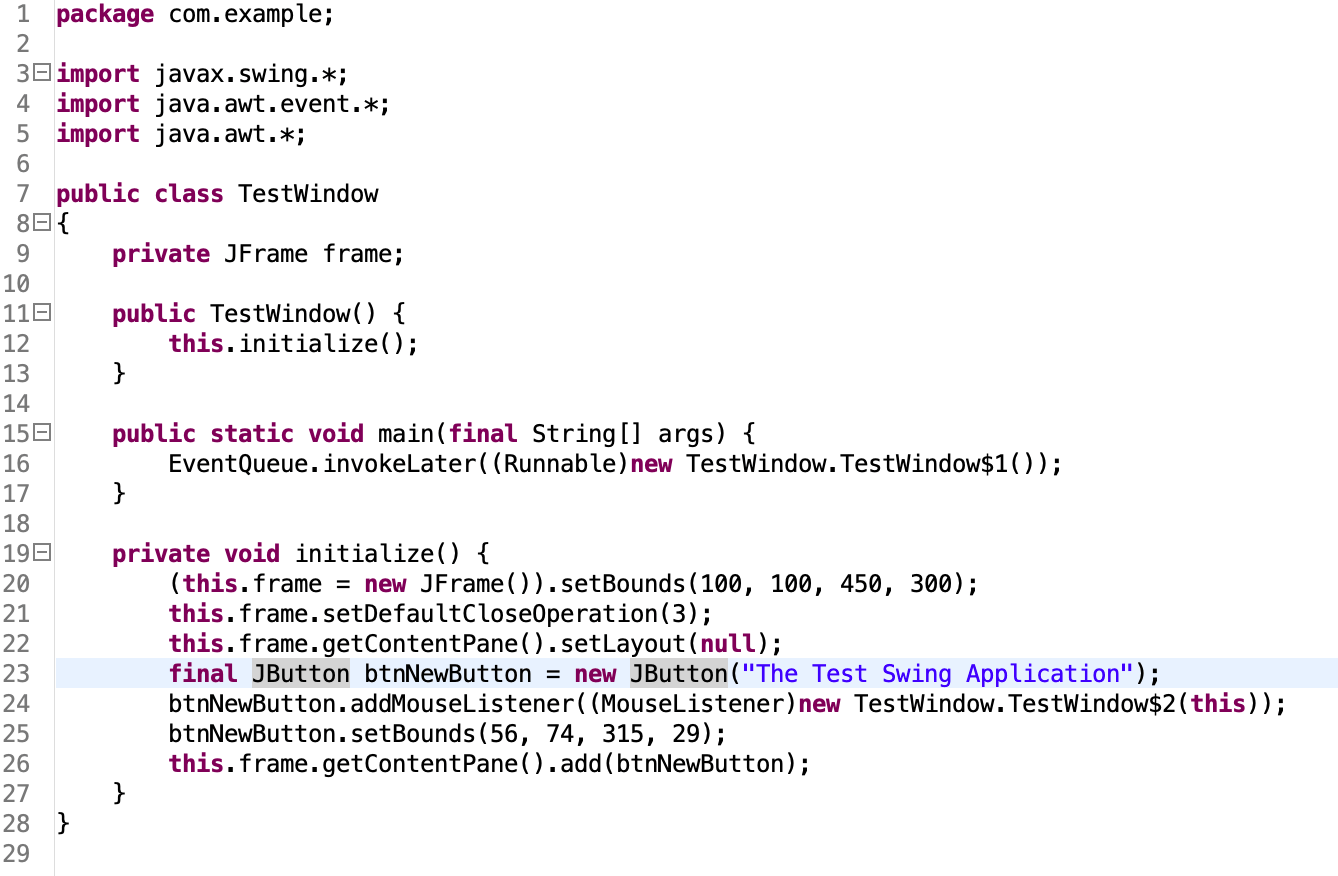
Click on com.example.TestWindow @0x0000…. and then click “Create .class File”
cd to the directory where the jhsdb command was executed before, you can see the generated class file

Use Luyten Or jadx to open the class file and you can see the decompiled code