Use vlx-vmengine for deobfuscation.
vlx-vmengine-jvm is a Java bytecode execution engine implemented in Java. Please refer to https://github.com/vlinx-io/vlx-vmengine-jvm for its usage.
There is a simple piece of Java code as follows:
class HelloWorld {
private String name = "";
public HelloWorld(String name){
this.name = name;
}
public void sayHi(){
System.out.println("Hi, " + name);
}
public static void main(String[] args){
String name = "George";
HelloWorld hello = new HelloWorld(name);
hello.sayHi();
}
}
After compiling into class files and obfuscating with a certain obfuscation engine, the following files are obtained:
After opening with jadx, it was found that apart from the main function, all other information is unrecognizable and the strings have been encrypted.
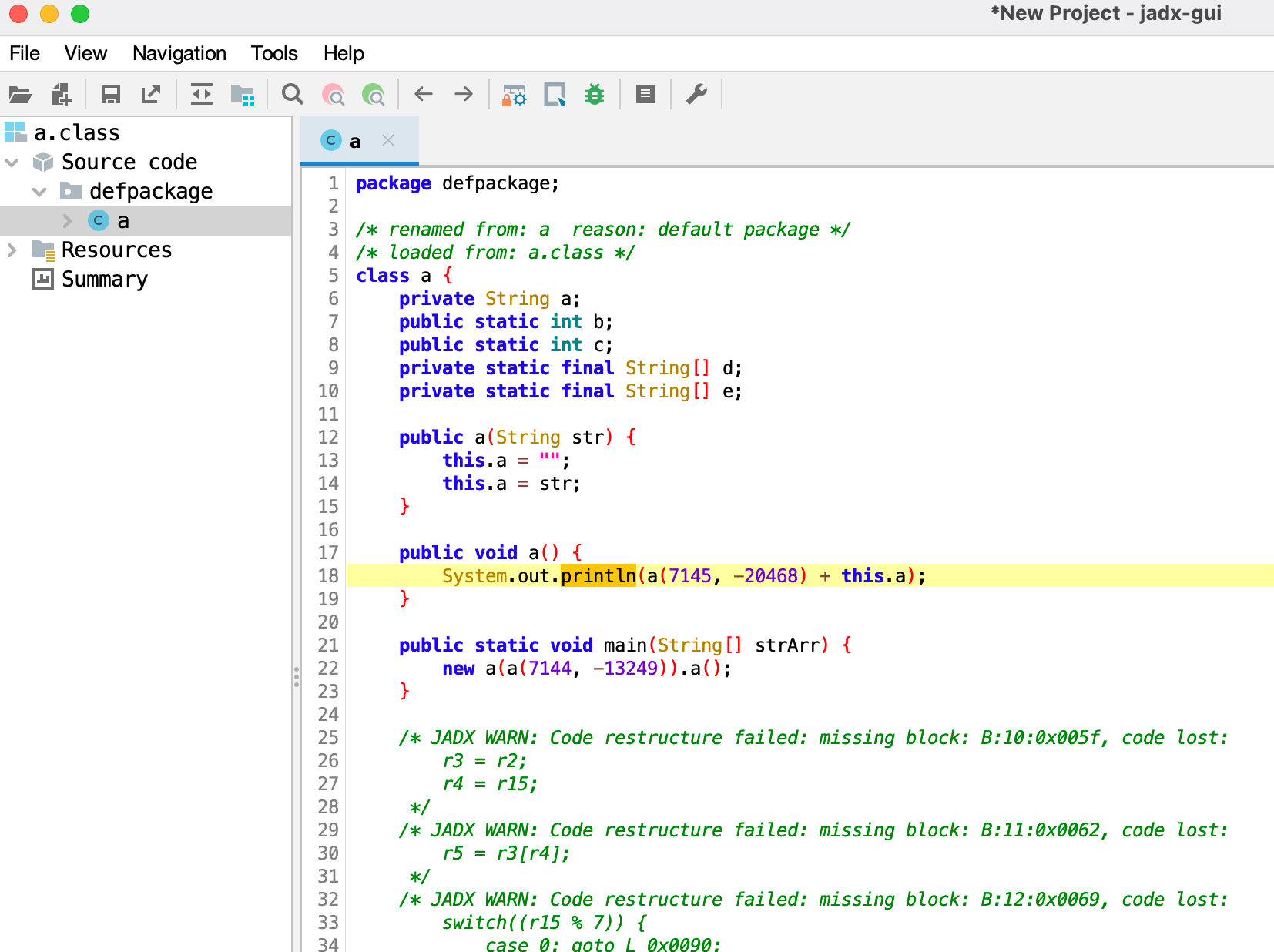
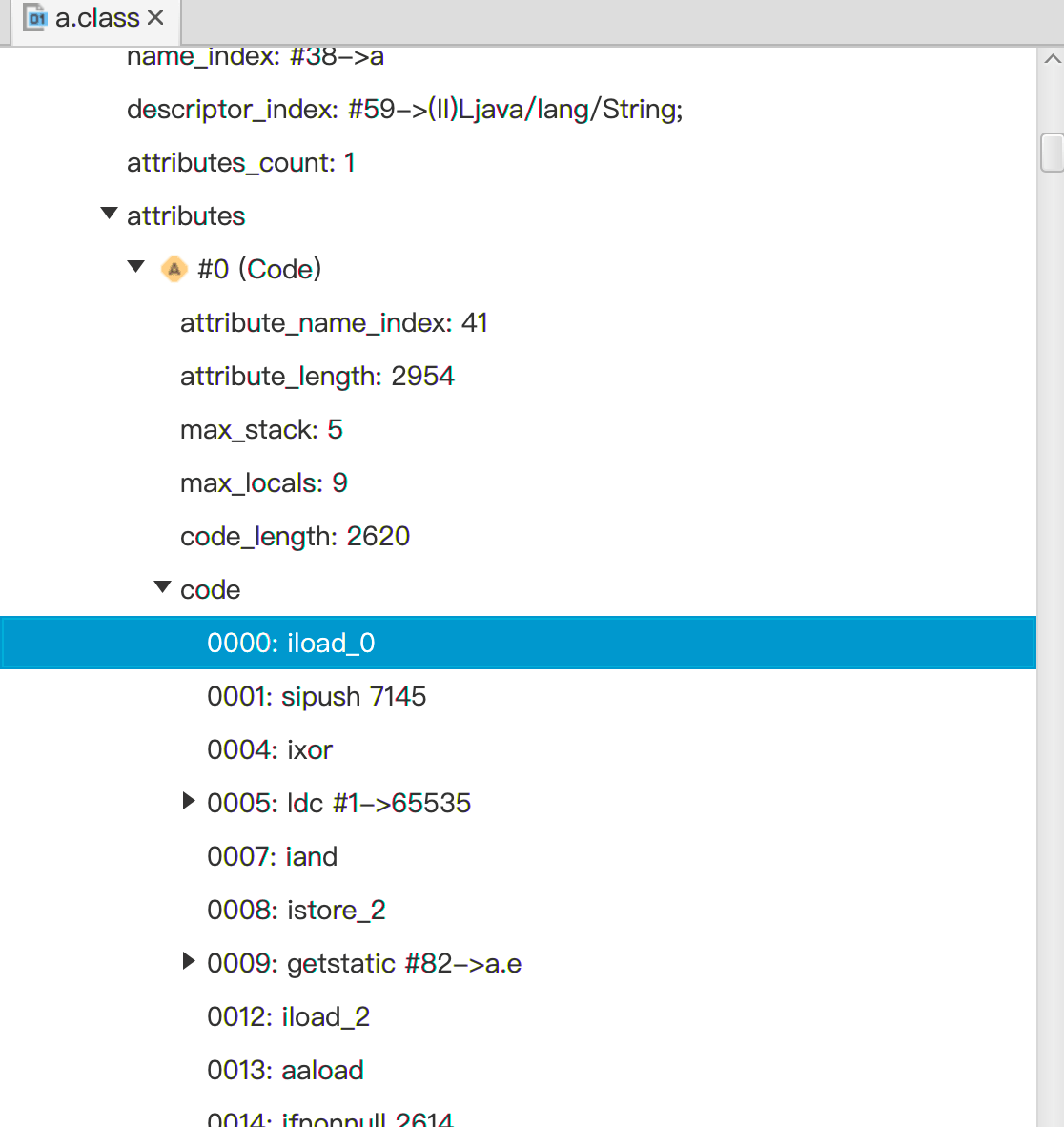
However, even if it is confused, the basic structure of the class and bytecode information still exist. Using ClassViewer to open a.class, you can see the methods and bytecode information of the class.
No matter how to obfuscate, it can only confuse the code at a static level and increase the complexity of analysis. In dynamic execution, it still needs to restore the original running logic of the program. Using vlx-vmengine-jvm to run the obfuscated code in the main method, we get the following output
2023-05-21 18:19:05 [DEBUG] LocalVars: [kotlin.Unit, kotlin.Unit, kotlin.Unit]
2023-05-21 18:19:05 [DEBUG] "L0: SIPUSH"
2023-05-21 18:19:05 [DEBUG] "push" 7144
2023-05-21 18:19:05 [DEBUG] "L3: SIPUSH"
2023-05-21 18:19:05 [DEBUG] "push" -13249
2023-05-21 18:19:05 [DEBUG] "L6: INVOKESTATIC"
2023-05-21 18:19:05 [DEBUG] "#20"
2023-05-21 18:19:05 [DEBUG] "class a, NameAndType(name='a', type='(II)Ljava/lang/String;')"
2023-05-21 18:19:05 [DEBUG] private static java.lang.String a.a(int,int)
2023-05-21 18:19:05 [DEBUG] "pop" -13249
2023-05-21 18:19:05 [DEBUG] "pop" 7144
2023-05-21 18:19:05 [DEBUG] Execute method: private static java.lang.String a.a(int,int)
2023-05-21 18:19:05 [DEBUG] Args: [7144, -13249]
2023-05-21 18:19:05 [DEBUG] "push" "George"
2023-05-21 18:19:05 [DEBUG] "L9: ASTORE_1"
2023-05-21 18:19:05 [DEBUG] "pop" "George"
2023-05-21 18:19:05 [DEBUG] "localVars[1] = George"
2023-05-21 18:19:05 [DEBUG] "L10: NEW"
2023-05-21 18:19:05 [DEBUG] class a
2023-05-21 18:19:05 [DEBUG] "push" InstanceToCreate(clazz=class a)
2023-05-21 18:19:05 [DEBUG] "L13: DUP"
2023-05-21 18:19:05 [DEBUG] "pop" InstanceToCreate(clazz=class a)
2023-05-21 18:19:05 [DEBUG] "push" InstanceToCreate(clazz=class a)
2023-05-21 18:19:05 [DEBUG] "push" InstanceToCreate(clazz=class a)
2023-05-21 18:19:05 [DEBUG] "L14: ALOAD_1"
2023-05-21 18:19:05 [DEBUG] "#1"
2023-05-21 18:19:05 [DEBUG] "push" "George"
2023-05-21 18:19:05 [DEBUG] "L15: INVOKESPECIAL"
2023-05-21 18:19:05 [DEBUG] "#47"
2023-05-21 18:19:05 [DEBUG] "class a, NameAndType(name='<init>', type='(Ljava/lang/String;)V')"
2023-05-21 18:19:05 [DEBUG] public a(java.lang.String)
2023-05-21 18:19:05 [DEBUG] "pop" "George"
2023-05-21 18:19:05 [DEBUG] "Execute new instance: public a(java.lang.String)"
2023-05-21 18:19:05 [DEBUG] "Args: [George]"
2023-05-21 18:19:05 [DEBUG] "pop" InstanceToCreate(clazz=class a)
2023-05-21 18:19:05 [DEBUG] "L18: ASTORE_2"
2023-05-21 18:19:05 [DEBUG] "pop" a@4612b856
2023-05-21 18:19:05 [DEBUG] "localVars[2] = a@4612b856"
2023-05-21 18:19:05 [DEBUG] "L19: ALOAD_2"
2023-05-21 18:19:05 [DEBUG] "#2"
2023-05-21 18:19:05 [DEBUG] "push" a@4612b856
2023-05-21 18:19:05 [DEBUG] "L20: INVOKEVIRTUAL"
2023-05-21 18:19:05 [DEBUG] "#54"
2023-05-21 18:19:05 [DEBUG] "class a, NameAndType(name='a', type='()V')"
2023-05-21 18:19:05 [DEBUG] public void a.a()
2023-05-21 18:19:05 [DEBUG] "pop" a@4612b856
2023-05-21 18:19:05 [DEBUG] Execute method: public void a.a()
2023-05-21 18:19:05 [DEBUG] Receiver: a@4612b856
2023-05-21 18:19:05 [DEBUG] Args: [a@4612b856]
Hi, George
2023-05-21 18:19:05 [DEBUG] "L23: RETURN"
From the console output, we can see that the program has restored its original behavior, which is to print Hi, George. At the same time, from the output, we can also determine that the decryption function for strings is in private static java.lang.String a.a(int,int), with parameters 7144 and -13249. If we continue to use vmengine to debug the a.a(int,int) method, we can discover the string encryption method used by this obfuscation engine.